Yesterday, an unusually dangerous security vulnerability in macOS 10.13.1 High Sierra was uncovered. Less than 24-hours later, Apple has issued a patch to correct the situation. The vulnerability allowed access to the Unix ‘root’ account – the most powerful ID on a Unix system – without the use of a password.
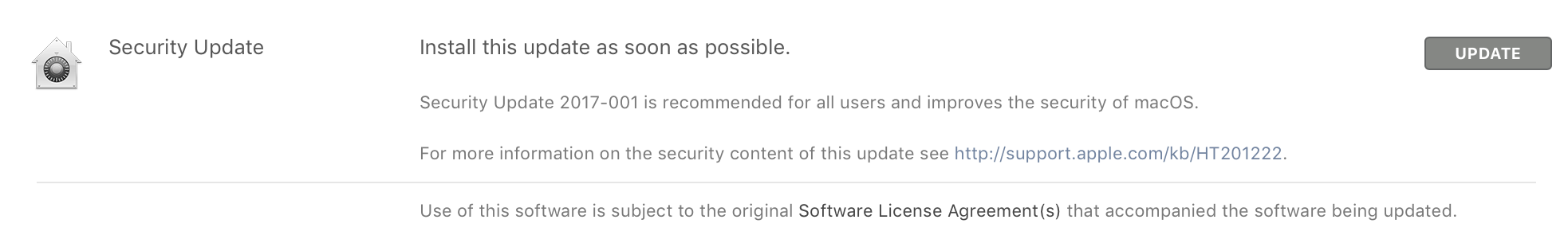
Apple support article HT208315 gives you the specifics about this vulnerability. If you haven’t already done so, go to the Mac App Store and install Security Update 2017-001. It is a small update that does not require the Mac to be rebooted.
John Gruber over at Daring Fireball received a statement from Apple stating the company’s regret and apology for rolling out High Sierra 10.13.1 with this bug in it. The statement to Daring Fireball also noted that “starting later today it will be automatically installed on all systems running the latest version (10.13.1) of macOS High Sierra.”
It was later reported, again by Gruber, that the Security Update 2017-001 patch inadvertently breaks file sharing in macOS High Sierra. If you experience the post Security Update 2017-001 file sharing bug, Apple has posted support article HT208317 on how to fix file sharing. To apply the file sharing bug fix, open Terminal.app and issue the command:
sudo /usr/libexec/configureLocalKDC
There is no output from the command. When you are done, quit Terminal.